
Contact us
Our team would love to hear from you.

In this article, we’ll examine the challenges of developing a robust application from multiple legacy platforms, how to approach the process, and the key aspects that should be considered.
Many long-established companies have likely encountered the difficulties associated with managing one or more legacy systems. As organizations expand their service offerings and create applications for each service, they often become burdened with outdated systems. These legacy systems jeopardize not only customer experience and retention but also security, compliance, effective resource allocation, and operational efficiency. Application modernization addresses the risks and issues associated with legacy systems, making software resilient and reliable.
A comprehensive approach to legacy system modernization, especially when consolidating several different systems into an all-in-one solution, aims to create a powerful new system that improves a company’s processes. To ensure the performance, flexibility, and scalability of the new application, it’s crucial to adhere to the following effective approaches.
The SAFe (Scaled Agile Framework) methodology is an iterative approach to project management that is suitable for large enterprises. It involves applying Agile practices to development projects to increase flexibility and improve control. Product development is divided into different streams across various teams working independently, each with clearly defined roles and responsibilities. This structure makes complex projects easier to manage.
When dealing with legacy systems, migration helps resolve compatibility issues and enhance the availability and security of the system. To allow the concurrent operation of the legacy systems alongside the new application before full replacement, both systems are operated in parallel. This is necessary to validate the new application against the legacy system.
Event-driven implementation for data access enables a system to act on events (such as the pressing of a button) as they happen. This approach is suitable for the independent development and deployment of the system, achieved through the decentralization of responsibilities. In this scenario, the new application operated independently from the legacy software, not relying on its performance, thereby enabling scalability and real-time processing and analytics.
When building a reliable, high-quality product from a legacy system, a testing pyramid is an effective approach. This includes unit, integration, and end-to-end (E2E) tests, offering a comprehensive and efficient method for maintaining and improving the application by dividing and balancing the testing efforts at different levels.


The following infrastructure elements play a key role in transforming multiple legacy systems into a powerful modern solution.
As the cornerstone of customer engagement, the client-facing side of an application should be well-designed, intuitive, and functional. Legacy app modernization provides an opportunity to add features that were lacking in the old system and improve the interface, enhancing user experience.
An admin panel is a core component of an application that gives administrators the tools they need to manage, control, and configure the system. It also displays all the data the system is designed to collect, such as customer details, operational status, and more. Admin dashboards allow companies to monitor and analyze product performance, facilitating prompt decision-making and action.
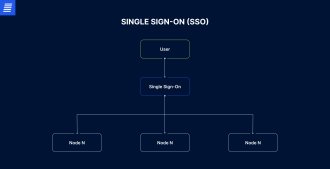
SSO is an authorization protocol that allows users to log into multiple applications with one set of credentials. When transforming multiple legacy systems into a modern solution, SSO can streamline the user experience, enhancing both convenience and security while the legacy application transformation is in progress.

Security is one of the main issues with legacy systems. When modernizing outdated software, it’s important to integrate security measures from the early stages to ensure that the new solution meets all requirements.
This is an important functionality for enhanced user experience. The system should be able to send notifications through different channels, such as push notifications and email, and alert users about relevant events (changes in policy, new features or services, proposals, etc.).
Data plays a significant role in helping companies develop strategies. Systems require reporting capabilities to collect and present data in a clear, structured format, which enables a comprehensive view of business dynamics. With data analytics capabilities, companies can gain valuable insights and identify patterns essential for informed decision-making.

A centralized data warehouse and Microsoft Power BI allow collecting and analyzing data from the divisions scattered across the USA.
Logging and monitoring ensure that the system is secure, fully functional, and demonstrates optimal performance. This unified approach to tracking and managing system activities enables prompt identification and resolution of issues and errors, ensures the system is compliant with the relevant regulations, detects malicious activities, and prevents or mitigates cyberattacks.
If the new application is intended for an international audience, localization and internationalization are crucial aspects of the development process. Localization and internationalization frameworks ensure dynamic content translation based on regional and user settings. The modernized application should support right-to-left languages and layouts for different text directions. By setting up a localization platform integration with the code repository, new and updated translations can be automatically integrated into the application, accelerating time to market.
When it comes to modernizing a legacy system, let alone multiple systems, security is one of the primary considerations. The new application should address the faults and vulnerabilities of the outdated software, protect sensitive data, comply with local legal requirements like GDPR, and prevent cyberattacks. This is achieved by integrating security measures throughout the entire application modernization process.
Each industry has a set of policies or security requirements that regulate data protection and privacy. Noncompliance with these standards can lead to lawsuits and financial and reputational losses.
Systems consist of numerous interdependent components, such as libraries, frameworks, and other systems. To avoid errors and security breaches when modernizing legacy systems, these dependencies must be properly managed. There are tools designed to automate dependency checks and provide security alerts, ensuring the security and reliability of the system.
Error monitoring tools facilitate real-time tracking of problems, allowing for quick detection and resolution and offering insights into their underlying causes.
Incorporating security measures into the CI/CD pipeline enables continuous monitoring and helps identify potential security threats and vulnerabilities in the system, protecting it against cyberattacks.
Access to sensitive data should be controlled throughout the development process. Secure storage and data backup are also key measures to ensure data safety and availability in case of any disruptions.
Legacy systems typically lack scalability, which impacts performance, workload handling capacity, infrastructure costs, functionality, and even customer satisfaction. Several practices can ensure that a modernized application is scalable and resilient, guaranteeing high availability and consistent performance.
Microservices architecture involves breaking the system down into independent services. This approach facilitates scaling each service separately according to specific needs, thereby avoiding unnecessary resource expenditure.
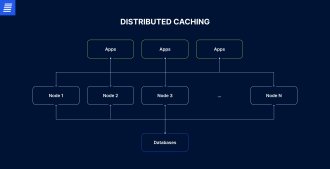
Distributed caching involves storing data across multiple nodes of a network system. This is crucial for applications with high data loads and volume because distributed caching increases processing power, lowers response time, and reduces the load on databases.

Breaking down procedures into independent tasks allows for asynchronous processing, so processes can be handled separately without having to wait for other tasks to be completed. This improves system performance and enables efficient scalability.
Continuous monitoring of system performance is essential for promptly identifying and resolving any issues, including scaling bottlenecks. This ensures that the system can effectively manage increasing workloads.
Legacy app modernization is an important step toward new opportunities and business growth. Modernized solutions come with enhanced security, improved performance, upgraded flexibility, and many other benefits. Though modernization is a complex process, a skilled development partner can ensure the process runs smoothly and the new system meets all requirements and objectives. Ready to launch your project? Contact our experts to learn more and get started.

A legacy system or application is computing software that is based on outdated technologies but is crucial to a company’s operations. These systems are characterized by limited flexibility, scalability, and integration opportunities as well as low performance and weak security.
There are seven main application modernization approaches: encapsulation, rehosting, replatforming, refactoring, rearchitecting, rebuilding, and replacing. The choice of legacy application modernization strategy depends on the company’s needs and requirements, the current state of the system, and the budget.
The approach to legacy application modernization determines the process. You can begin by teaming up with a skillful partner who will evaluate the complexity of the project, define the goals, and develop an effective plan. Contact our experts to begin collaboration.
Can’t find the answer you are looking for?
Contact us and we will get in touch with you shortly.
Our team would love to hear from you.
Fill out the form, and we’ve got you covered.
What happens next?
San Diego, California
4445 Eastgate Mall, Suite 200
92121, 1-800-288-9659
San Francisco, California
50 California St #1500
94111, 1-800-288-9659
Pittsburgh, Pennsylvania
One Oxford Centre, 500 Grant St Suite 2900
15219, 1-800-288-9659
Durham, North Carolina
RTP Meridian, 2530 Meridian Pkwy Suite 300
27713, 1-800-288-9659
San Jose, Costa Rica
C. 118B, Trejos Montealegre
10203, 1-800-288-9659