
Contact us
Our team would love to hear from you.

Penetration testing has become a common practice for companies in many fields, but it is especially important for organizations that store personal and sensitive data. It ensures that your security control works and that your team knows how to act in the event of an attack. In this article we will define penetration testing and describe the approaches, types, and stages that it involves.
Penetration testing, also known as pen testing, is a type of security testing that is performed to determine and eliminate any security issues. It helps a company to check its response to attacks and risk prioritization, find flaws in the security design and control components, and examine how the organization maintains compliance with its standards and regulations.
The professionals in this field can be called ethical hackers. Their job is to find a breach in the system and simulate a cyber-attack in a controlled and secure environment. Penetration testing is more than just an automated scanning – it is a realistic imitation of a threat performed by skilled professionals.
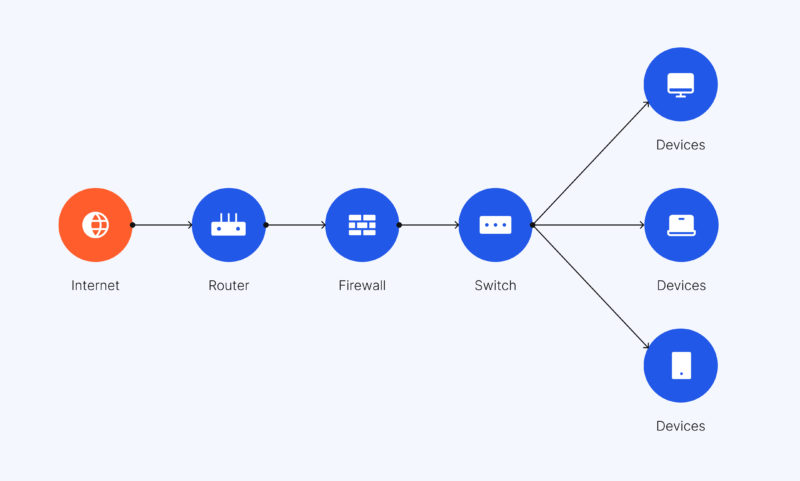
What is pen testing and why is it important
There’s no doubt that security is one of the fundamentals of software system reliability, and penetration testing is one of the best ways to evaluate its effectiveness. In addition to security, software system reliability also implies system’s observability and scalability. This means that there’s a possibility that data sources may be improperly filtered or structured, making them invisible and causing a critical condition to be overlooked. Moreover, the amount of processed information and the workload are constantly expanding, which increases the system’s vulnerability to external attacks. That’s why IT infrastructure requires special attention from QA specialists.
The 3 types of penetration testing approaches differ in the amount of information given to the QA team.

Application security testing approaches
With this approach, the QA specialist is provided with full information about the system and the network, including source code, IP address, etc. The aim of the white box approach is to carry out in-depth research on a particular system component. Its main advantage is that it saves time and simulates a targeted attack on a specific infrastructure element using different attack vectors. However, with the unlimited access to the company’s data given to the tester, it may be difficult to decide what aspect of the system to focus on first.
In this approach to pen testing, the QA specialist has access only to publicly available information about the system and acts as authentically as possible. This is the costliest approach as it requires a more extensive set of skills and takes more time to complete. At the same time, this is the most accurate penetration testing methodology as it demonstrates how an attacker can compromise an organization using freely accessible information.
This approach is an intermediate between the white and black box. The QA specialist has a limited amount of information (e.g., a personal login and a password). The main point of assessment is to determine how long it takes for an intruder to increase their access from a privileged user to a domain admin. One of the key advantages of the gray box pen testing is that it provides a more focused and thorough analysis of a particular system component. It offers a good balance between accuracy and depth.
There are different types of penetration testing. They can be divided into two groups: remote and on-site testing. The choice of a pen testing type depends on the target, infrastructure, and a system component it affects, as well as the company’s needs, objectives, and strategy.
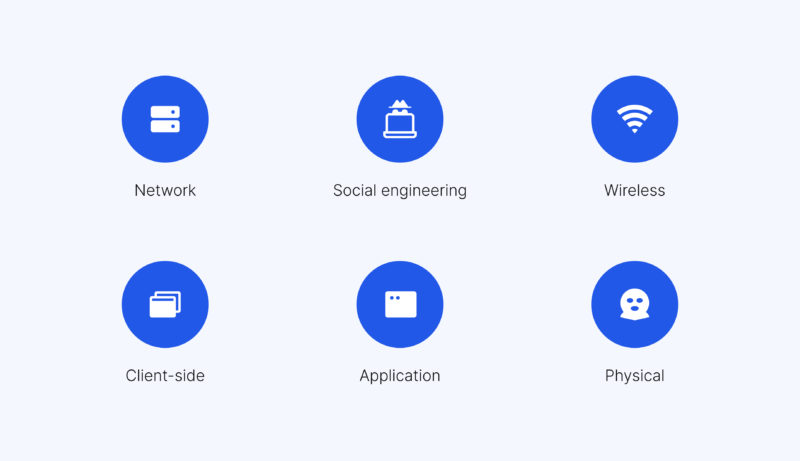
What are the different types of penetration testing?
The types of pen testing in which the QA team works remotely are more technically complex. That is when EffectiveSoft can offer professional help and provide a thorough examination of your company’s security system.
This is one of the most frequently performed types of penetration testing. The key objective of the network pen testing is to identify vulnerabilities in a company’s infrastructure, including such assets as firewalls, servers, system hosts, routers, switches, etc.
This type of testing helps to check the network and the system before they are used or according to a testing plan. Network pen testing can be applied inside the corporate network and for Internet-facing systems.
Application pen testing examines the weaknesses of web-based and mobile applications and their components. The QA team tries to damage the functioning of an application and to acquire sensitive information. Knowing all the security gaps and vulnerable parts of the application makes it easier to improve its code and design.
Client-side pen testing is used to check the security control of software running on users’ computers. Such software includes web browsers, email, messaging applications, file-sharing applications, anti-virus software, content creation software, etc. Penetrating client-side applications gives attackers easy access to corporate IT infrastructure. Vulnerabilities and weaknesses in this type of software can be harmful to a company’s entire security system.
Social engineering attacks rely on human interaction, and no one is safe from fraud. Social engineering pen testing involves manipulating users into giving sensitive information and then using it to extend privileges. It helps to determine how far into the system it is possible to penetrate using the acquired information.
The following are some of the common types of cyber-attacks simulated by social engineering pen testing:
Social engineering pen testing and raising awareness among employees about the policy against the mentioned cyber-attacks help to minimize the risks of such attacks.
The following types of penetration testing require the QA team to be present on-site:
Wireless pen testing means that a QA specialist examines the wireless local network including all the devices connected to it and all the wireless protocols. This testing helps to review the level of defense against unauthorized access to the company’s wi-fi and data. It is implemented on-site as the QA team requires connection to the wireless signal.
This test is used to find and estimate the weaknesses in physical control. It involves obtaining physical access to the server or a sensitive facility. The physical security system should prevent an intruder from entering the facility and damaging the internal infrastructure. This security system may consist of locks, cameras, sensors, barriers, doors, or pass entry systems.
Penetration testing comprises different stages. They can vary depending on the testing type and the used approach, but the main five stages are:
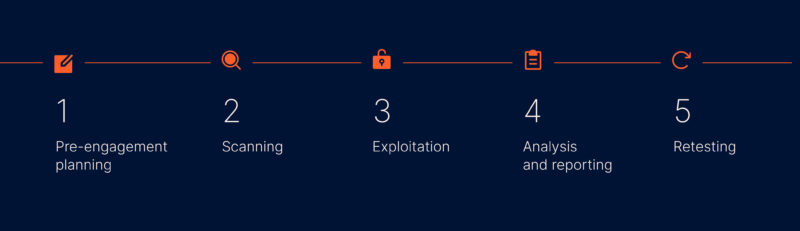
5 stages of penetration testing
This stage includes deciding on the objectives, scope, and limits of the test. It also involves collecting all the necessary information about the company and the system that is going to be tested, as well as choosing the testing method.
At this stage the QA team looks for vulnerabilities, potential access points, and security gaps in the system. The team also identifies the nature of these gaps and the ways they can be exploited.
The exploitation stage involves making use of the detected security gaps. This stage can be divided into two main steps: gaining access and maintaining it. The QA team breaks into the system through the discovered access points and finds all the possible ways to promote their privileges within the system.
Upon testing, the QA specialists provide a review describing all the vulnerable elements of the system that require extra attention. Another important step of this stage is developing a plan for eliminating the risks and improving security control. Then, the changes are implemented according to the report.
After all the alterations are made, the QA team attempts to gain access again. They check the updated system control and determine whether it is secure or its components need additional changes.
Knowing the types of penetration testing helps to better understand the process itself and how it improves the workflow, making it easier to choose which type would benefit your company. It’s also important to choose experts in the field who can find all of your system’s vulnerabilities and remedy them as quickly as possible.
With the help of the experienced EffectiveSoft team you can be sure that QA testing services (penetration testing in particular) will be completed with the right methods and tools that correspond with your company’s objectives and needs. Contact us to learn more.
Our team would love to hear from you.
Fill out the form, and we’ve got you covered.
What happens next?
San Diego, California
4445 Eastgate Mall, Suite 200
92121, 1-800-288-9659
San Francisco, California
50 California St #1500
94111, 1-800-288-9659
Pittsburgh, Pennsylvania
One Oxford Centre, 500 Grant St Suite 2900
15219, 1-800-288-9659
Durham, North Carolina
RTP Meridian, 2530 Meridian Pkwy Suite 300
27713, 1-800-288-9659
San Jose, Costa Rica
C. 118B, Trejos Montealegre
10203, 1-800-288-9659